SaaS applications can be deployed in a variety of ways to help grow your business and and build processes at scale. However, even with these tools, identity management, authorization, and user management can still remain a challenge.
In this article we’ll take a look at how you can use Active Directory with your favorite SaaS applications to improve your processes and workflow as well as the pros and cons of different solutions.
In general, onboarding users can be a time-sensitive and manual process that involves using the right administrators across multiple departments to manage the entire process. Additionally, in many organizations, the Microsoft Active Directory (AD) functions as the administrative user directory that grants access to essential IT services, in particular email and file sharing.
Many enterprises have leveraged Software-as-a-Service (SaaS) since Salesforce launched almost two decades ago.
Popular vendors like Adobe, Oracle, and Microsoft have successfully moved their core applications to subscription-based models.
Other vendors including Box and ServiceNow have completely replaced on-premises solutions with cloud-based solutions, SaaS is now the preferred way companies consume core business software.
What is a SaaS Application Integration?
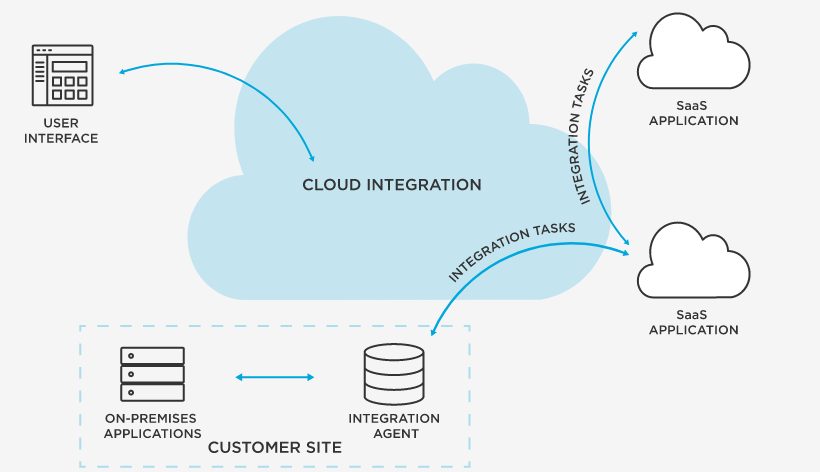
SaaS data integration is the process of distributing applications to your team or anyone within your company conveniently, securely, without configuration. This process enables you to easily and accurately share access to applications.
You’re also able to work effectively from that ambiguous cloud that’s the talk of the town, without going through the public domain. The vast majority of SaaS integrations are cloud-based.
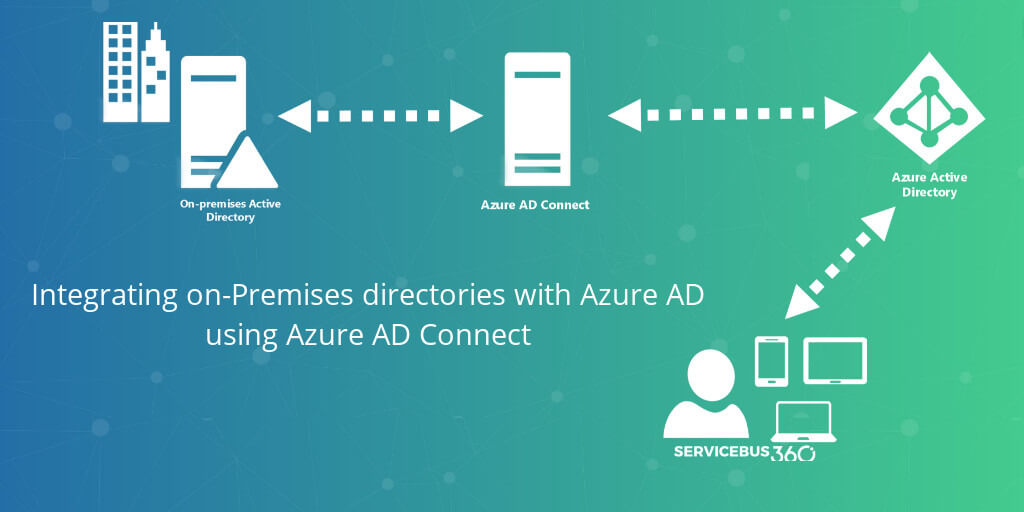
How Does Active Directory Integration Work?
The process isn’t as complicated as it sounds. Let me show you how it works:
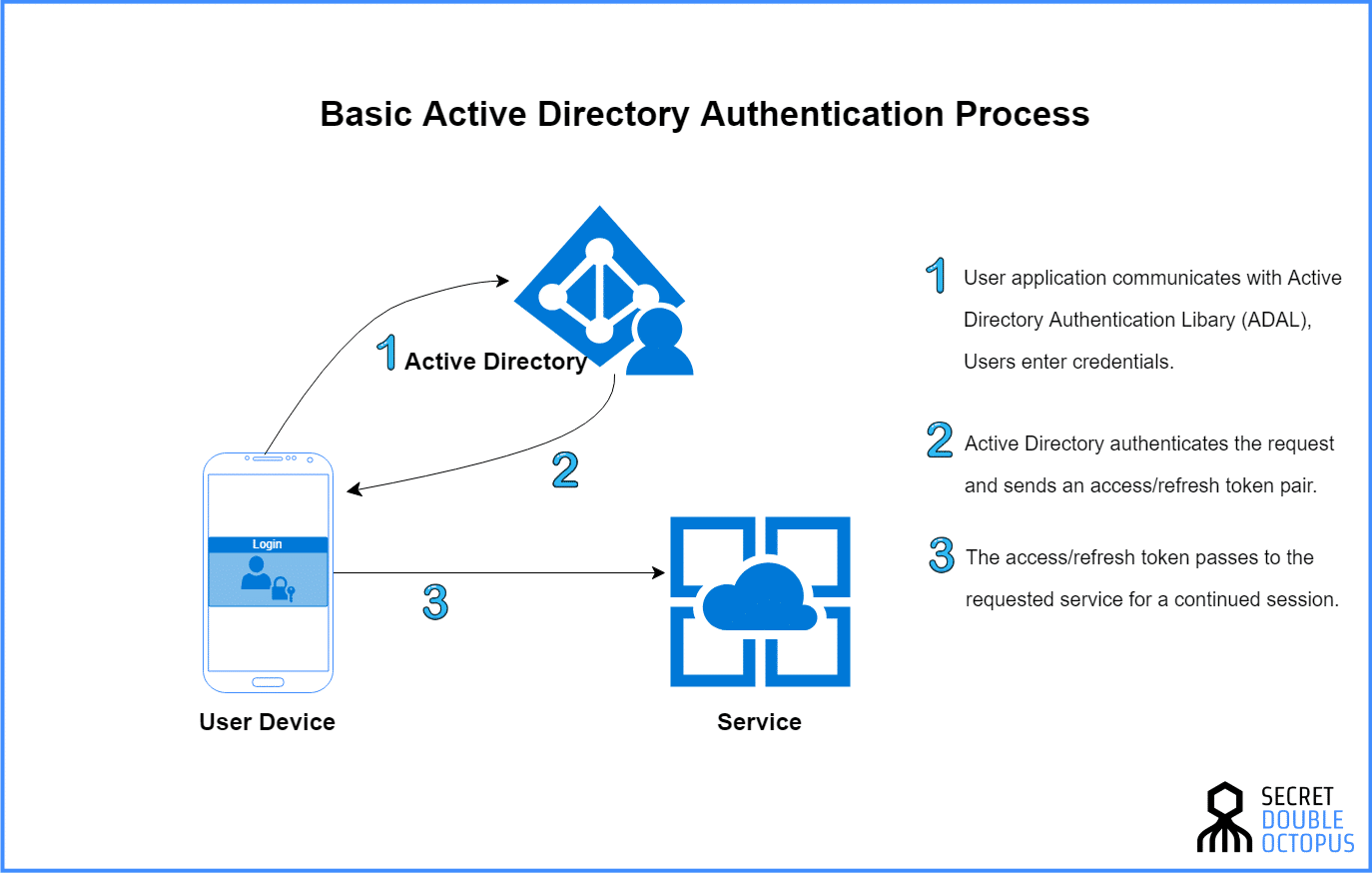
When a user logs into a web application, a program, or software, the username and password are passed and verified against your existing infrastructure to make sure the user’s credentials are valid.
Here’s what it looks like, illustrated below:
Of course, without the right credentials, the user will be shut out. Think Rundeck!
Depending on the provider, the application will usually request a set of fields once the user’s credentials are valid.
These sets of fields will stem from your Active Directory infrastructure (some providers will only request first name, last name, email, and samaccountname.)
When the Active Directory infrastructure has successfully returned the set of information about the user, the user’s application account will be created or updated—the goal is to keep all the vital information in-sync.
Note: Only a handful of applications automatically update Active Directory fields—which typically will prompt the user to log-in. Alternatively, an admin can manually run a synchronization from within the application.
Here are the three most effective ways of integrating Active Directory with your SaaS applications:
Integration #1. Microsoft AD FS
When Windows Server 2008 R2 was launched, Microsoft built off the momentum with the release of Active Directory Federation Services (AD FS) 2.0.
The goal was to create a system that’s responsible for providing an extensible platform that can handle single sign-on with applications outside of the firewall.
This new system makes it possible for organizations to leverage AD FS to address the SSO requirement of an AD integration. Sadly, the downside is that it doesn’t address user synchronization, neither does it address user provisioning or de-provisioning.
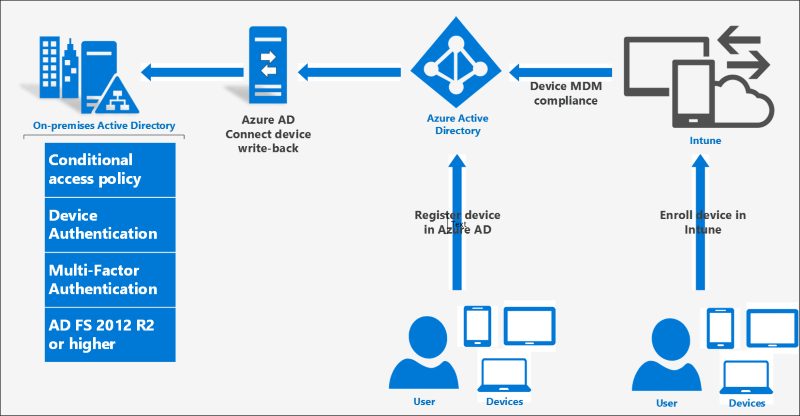
Since the release of Windows Server 2009 and subsequent launches, there are some updates to protected logins now, including:
i). External Auth Providers as Primary: This allows users to use third-party authentication products as the major factor, instead of revealing password as the first factor. It can claim MFA if the external auth provider requires 2 factors.
ii). Pluggable Risk Assessment Module: It’s now easier for users to build their own plug-in modules, which can help them block specific types of requests during the pre-authentication stage.
In turn, users can easily use cloud intelligence such as Identity protection to block logins due to risky users or risky transactions.
With these new updates, the user data is in safer hands. However, it’s quite imperative to consider the platform you’re using when considering AD FS as a viable means to address SSO needs.
As a core feature of Windows Server, AD FS was primarily developed as a platform—not an end-to-end solution for authenticating single sign-on needs. Although these platforms can be powerful and flexible, they require signifiant amounts of additional work to develop a complete solution.
Integration #2. Use a Third-Party Vendor Solution
Given the accelerated deployment of SaaS applications, there are many vendors you can leverage to address your enterprise’s Single Sign-On and user management needs.
Some of the vendors include:
- JumpCloud;
- Okta;
- OneLogin;
- Oracle Identity Management, etc.
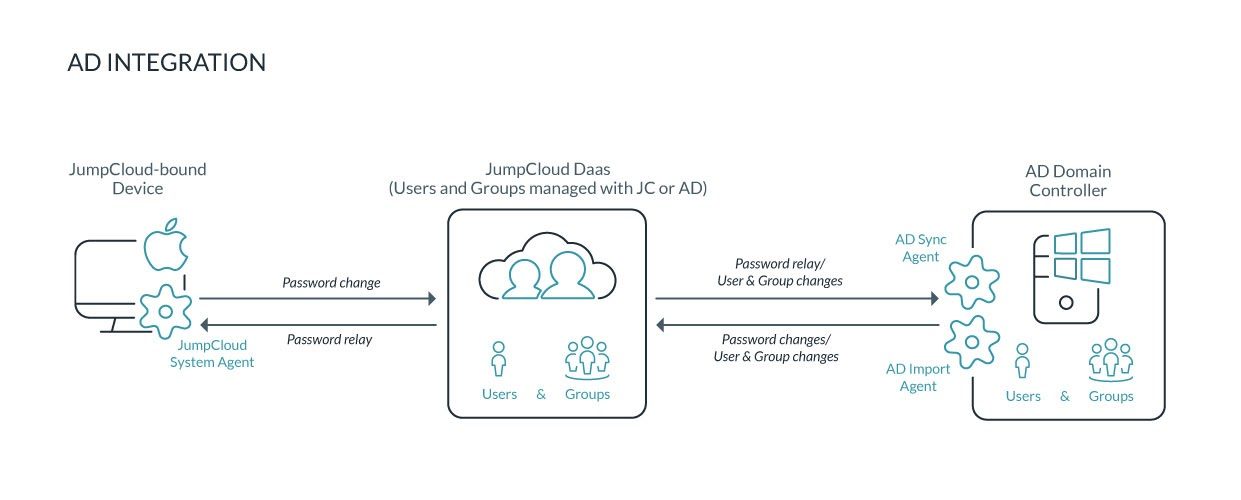
JumpCloud is our organization’s favorite vendor solution. The illustration below shows the simple process of AD integration using JumpCloud:
To successfully evaluate these vendors, it’s important to understand their abilities to integrate with Active Directory.
Greg Keller, in this Whiteboard Video Series, shares some thoughts on how the JumpCloud Directory-as-a-Service works. With additional videos found here.

Unlike an application-specific integration strategy, these vendors are designed to provide a single point of integration—especially with your on-premises Active Directory—which can then be used across all of your SaaS applications.
And quite different from the AD FS option, some vendors also offer a robust and comprehensive solution that is maintained for you. This is aimed at working seamlessly with your existing AD infrastructure but comes at a cost.
Integration #3. Independent Integrations With AD
You can quickly develop a custom integration with Active Directory yourself—when you take advantage of the AD integration tools offered by the most established SaaS applications and platforms.
For example, Google Apps, Salesforce, and Microsoft Online Services all play key roles when you’re considering independent integrations with AD. Surely, they all have their challenges as well, none of them are 100% flawless.
Google Apps Directory Sync, for example, is one of those independent solutions that provide one-way user migration from Active Directory into a Google Apps account. It gives the user flexibility and the chance to define which user attributes are imported.
Keep in mind, though, the setup and administration are often separate from what’s obtainable with the Google Apps administration console, which is a can be a deal breaker for admins who want to force-manage the system from a locally installed utility instead.
Organizations look for additional flexibility can leverage another third-party integration if they want to use SSO. This can result in two separate administration models—as well as what the user intends to use for SSO and user management.
An independent integration with Microsoft Office 365 Directory Synchronization, for example, equally provides one-way pushing of users—from within the Active Directory into Office 365.
Administrators can seamlessly utilize this tool when they’re looking to both provision and de-provision users in Office 365. which is defined when users are added or removed from Active Directory.
Just like the Google Apps tool, this process requires a decoupling from the primary administration experience. This can be managed efficiently via the on-premises utility.
There’s no provision for SSO, so it will result in two separate administration models and user stores.
Salesforce has provided a set of APIs that let users design proprietary solutions, which can push users from AD and enable users to authenticate against AD, at the same time, mostly when accessing Salesforce.com.
Although at this time, there’s no available tool that can help accomplish either of these tasks. To achieve these integration requirements, organizations need to invest heavily in both development and maintenance systems.
As you can see, the downsides of integrating AD with independent vendors are fairly clear. For one, organizations are expected to install and maintain tools from each vendor which can be both costly and time intensive.
Additionally, when those tools are inaccessible, you’re left to develop its own vendor-based solution.
Let’s take a look at some active directory use cases.
Active Directory Use Cases (Examples)
1). Reduce the Time Spent Onboarding New Employees
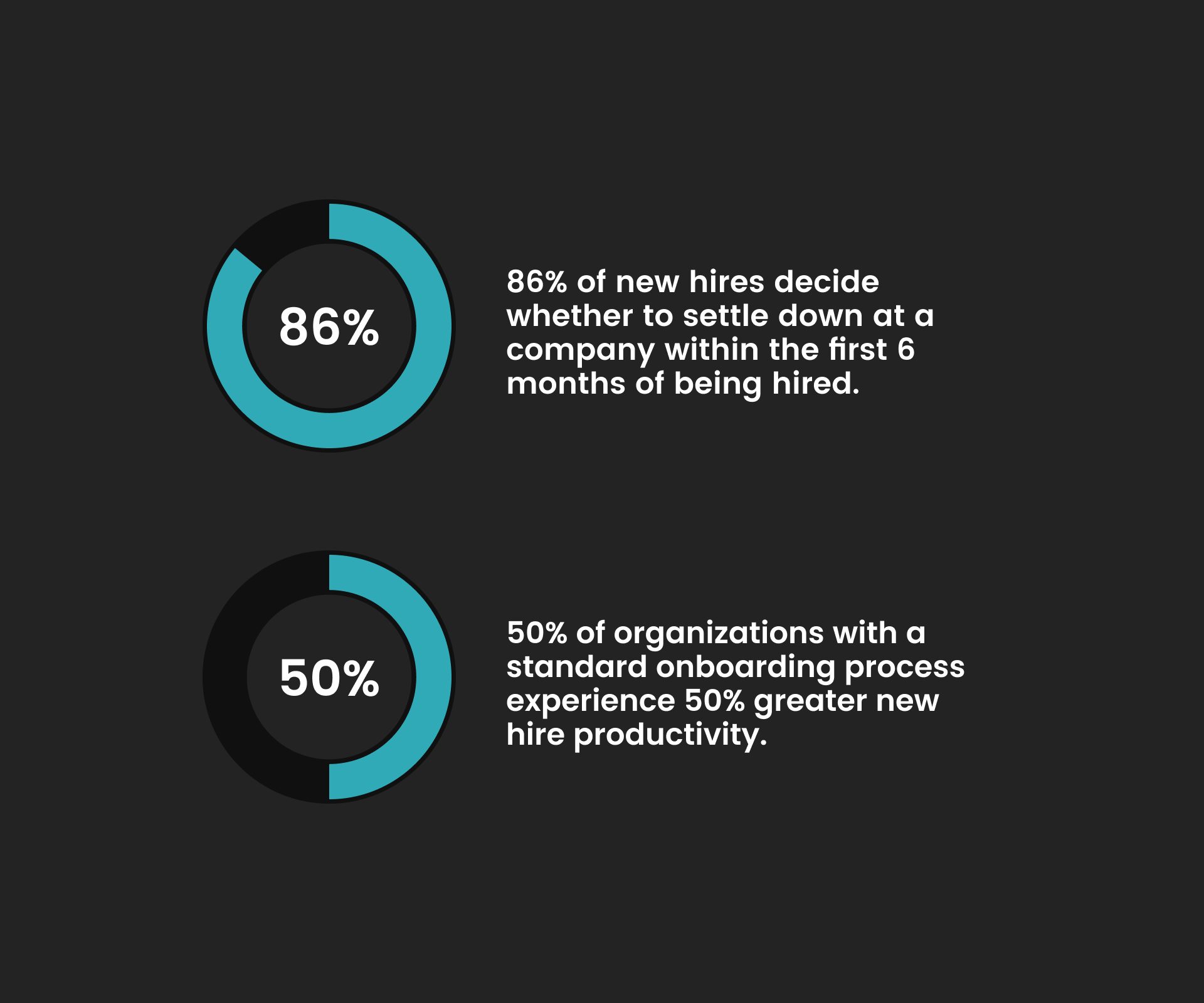
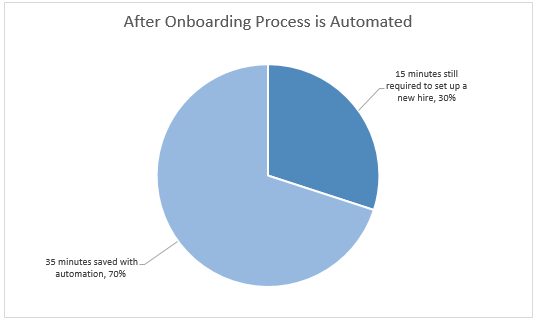
Active Directory (AD) integration with SaaS applications provides a means of minimizing onboarding time. It also simplifies the process; and automates every manual input—making onboarding over 50% more efficient.
A great example of how AD can reduce onboarding time is Nome Public Schools.
Before integrating its system with Active Directory, Nome Public Schools used to spend roughly 600 hours/year on provisioning, deprovisioning, and password resets.
Today, the organization uses JumpCloud AD and spends less than 100 hours/year on the same tasks.
Onboarding goes beyond hiring new employees. It’s also about improving employees’ experiences and putting them in position to do their best work. By making it easy for them to use tools they need to be effective and productive you can significantly reduce turn over and build a strong company culture.
In most organizations, it’s the duty of the HR teams to enter the new hire’s personal information into the Human Resource Management System (HRMS), such as ADP or Workday.
Once that’s done, a service desk ticket is generated to help the system administrator to make a provision for the new employee in Microsoft Active Directory (AD) or any other vendor.
Suppose the HR manager is expected to export the employee’s details in a CSV file from their HRMS application and send them via email to the IT team—that’s a lot of work if done manually.
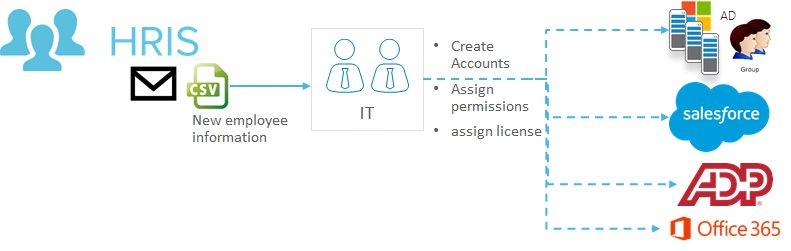
Working to automate user provisioning can help eliminate daunting and time-consuming onboarding operations like the example above. These integrations also help IT admins free up time to focus on other critical tasks that will move the organization in the right direction.
If your organization uses ADManager Plus, for example, you can automatically provision accounts in AD, Exchange, Office 365, Skype for Business, as well as G Suite. This will ensure that changes effected in the Human Resource Management Systems are reflected across all accounts.
Furthmore, you can take advantage of Connect iPaaS to eliminate the need to manually create and update identities in Active Directory—assuming the new hire record has been created or updated in ADManager Plus (ADP).
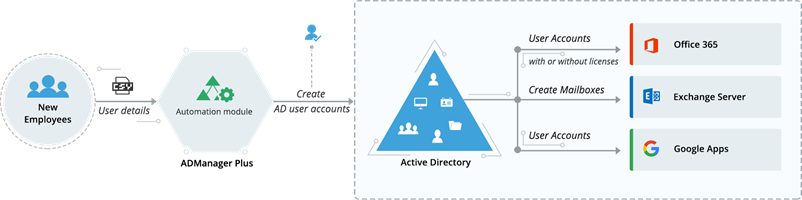
When the employee record is created or updated in ADP or Workday it is then synced to AD to create or update the user’s mapping groups. As a result, employee data can be synced instantly, saving hours of valuable time.
More effective onboarding allows you spend less time on admin tasks, and more time educating the new employee, improving the sales process, and ultimately make more money.
2). Efficient Asset Management Upon Onboarding
Passing the employee’s details to the IT department to notify them of the new hire is half the battle. Continued management of those assets often feels like a full time job.
By asset, I’m referring to the tools and creatives the employee needs to fully offer their best services to the organization. Comprehensive employee onboarding is a time-consuming process. It takes a lot of time to get a new hire and fully equip them to work.
Assigning a company email address, training, defining job roles, creating business accounts, resource allocation, and giving them company assets, requires massive amounts of coordination from multiple teams within the company.
To give you an idea, this process is well-illustrated in 3 steps:
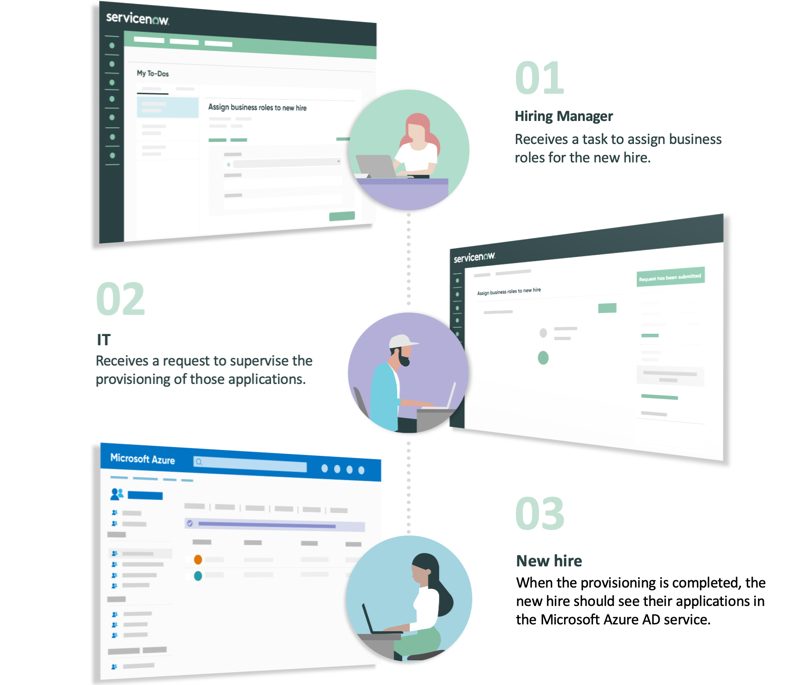
With Connect iPaaS, you can create workflows to automatically notify the teams concerned about the assets and accounts they need to create or allocate—the moment the employee’s identity has been created in Active Directory.
Another example, consider marketing certification for employees, an ADP will help you manage their assets accordingly.
My favorite example is Topgolf, a company that leveraged RoboMQ AD to catapult its IT integrations from managing just a few thousand employees to 24,000+ worldwide.
Consider services such as ServiceNow, Twilio, JIRA, Twilio, Slack, and other sales enablement tools; that can help act as connectors in Connect iPaaS and seamlessly integrate with AD to securely set up service desk tickets and notifications—thus offering a streamlined process for assigning assets to new hires.
3. Save Time Creating New Accounts in Enterprise Applications
Active Directory integration with your SaaS applications can also help you save time when creating new accounts in enterprise applications.
As you likely know, your employees’ data changes over time. They might get a raise, change names, or even leave the company. Having a streamlined process to update their account details and permissions can save a ton of time and headaches. Essentially, established organizations that use enterprise-level applications to onboard, nurture, convert new clients can also benefit from Active Directory integration. They can create trusted experiences with customers.
One of my favorite examples is Ally Financial, an organization that offers auto financing solutions. It capitalized on Okta’s AD solutions to provide a seamless and trusted experience for its 40,000 dealers (with varying data size). “This wouldn’t have been possible if it was done manually,” says Megan Crespi, CTO.
This site also employs AD to manage its onboarding process. Other popular eCommerce brands like Zappos, 3Wishes, and Aliexpress with hundreds of thousands of customers globally manage employee and customer onboarding easily with an AD.
And given both Amazon and eBay have their in-house AD, it’s always worth testing to see if it works for you.
While it’s important to integrate ADP or Workday to effectively create identities in AD, there’s more to consider when it comes to streamlining the employee onboarding process.
Whether you’re a medical practice that requires a simplified patient management system or a manufacturing firm, it’s become increasingly important to ensure downstream provisioning of Role-Based Access Control (RBAC) into your favorite productivity tools and enterprise-level applications. You can do this by implementing based on the rights and privileges granted to each specific employee.
At the end of the day, it just doesn’t make sense to spend hundreds of hours on tasks that can be easily automated.
In the case of onboarding, every task assigned to the employee needs to be synchronized with the appropriate department, especially for large digital organizations such as Shopify, Bluehost, etc.
While automating processes can take time initially, over time the dividends continue to pay off.
For large organizations that deal with thousands of employees, one simple automation or integration can dramatically improve company productivity and morale.
Conclusion
There you have it, several real world examples of how integrating your SaaS applications with Active Directory can improve your processes, productivity, and onboarding.
Active Directory can help you:
1.) Reduce the time spent on onboarding new employees.
2.) Help with efficient asset management during onboarding.
3.) Save time creating enterprise accounts.
And much more.
Keep in mind that modern identity management goes beyond connecting Active Directory with cloud applications. Assigning permissions and licenses in cloud applications is a critical step you must take as well. Services like vRealize, Okta, and JumpCloud can help you achieve simple and complex user provisioning in real-time.